Solid DNS (Part 3): BIND

BIND NOTE: You don’t have to install BIND, it is only required if you want to host your own authoritative zones locally (which I do). If you have no intention of doing this, you can skip this step entirely.
This guide is final stage in a three part series. If you haven’t already read Part 1: DoH using cloudflared and Part 2: Pi-hole be sure to check them out.
BIND
- Install BIND To install BIND on an Ubuntu system, its as simple as the following:
apt-get -y install bind9
- Configure BIND
Now you need to configure it. You MUST do this if you’re running Pi-hole & cloudflared on the same server. If you dont, BIND will try to start using port 53 (default DNS port) which Pi-hole is already running on .
In the folder /etc/bind you will find various configuration files. Using your favourite edit, modify the file /etc/bind/named.conf.options so that:
// forwarders {
// 0.0.0.0;
// };
Is replaced with (NOTE at bottom of page):
forwarders {
127.0.0.1 port 53 ;
};
And that:
listen-on-v6 { any; };
Is replaced with:
listen-on-v6 { none; };
listen-on port 5354 { 127.0.0.1; };
- Setup your local zones
Next, you will want to drop in any local or reverse zones into named.conf.local (also in /etc/bind). I prefer to break it up and also make a file called named.conf.reverse for my reverse lookups.
My file looks like this:
cat /etc/bind/named.conf.local
//
// Do any local configuration here
//
// Consider adding the 1918 zones here, if they are not used in your
// organization
//include "/etc/bind/zones.rfc1918";
zone "mycoolzone" {
type master;
file "mycoolzone.db";
};
Next you need to populate your zonefile. The default location for zonefiles on this installation will be /var/cache/bind. So my file looks something like this (its actually much larger but ive trimmed it down):
cat /var/cache/bind/mycoolzone.db
$ORIGIN .
$TTL 60 ; 1 minute
mycoolzone IN SOA dns1. root.mycoolzone. (
2018102901 ; serial
3600 ; refresh (1 hour)
180 ; retry (3 minutes)
2419200 ; expire (4 weeks)
60 ; minimum (1 minute)
)
NS dns-1.mycoolzone.
NS dns-2.mycoolzone.
$ORIGIN mycoolzone.
usg A 192.168.0.1
lounge-switch A 192.168.0.2
gaming-switch A 192.168.0.3
study-switch A 192.168.0.4
lounge-ap A 192.168.0.5
study-ap A 192.168.0.6
dns-1 A 10.152.0.3
dns-2 A 192.168.0.10
- Start BIND At this point, it’s actually safe to start BIND. We have already changed the port it is going to listen on, so there shouldn’t be a conflict. To start BIND, simply issue the following command:
systemctl start bind9
Check its status by running:
systemctl status bind9
- Setup forwarding for Pi-hole
Now you need to setup Pi-hole to forward DNS queries it receives for the above “mycoolzone” domain to BIND. This is super simple and only requires the creation of one file. In the folder /etc/dnsmasq.d/ create a file called 05-local.conf The file simply needs to look like this:cat 05-local.conf server=/mycoolzone/127.0.0.1#5354
Once you’ve saved 05-local.conf, you will need to restart Pi-hole to pickup this configuration. Simply type:
pihole restartdns
If you’ve completed everything correctly, you should now be able to query your DNS for mycoolzone:
dig @127.0.0.1 mycoolzone ns
; <<>> DiG 9.10.3-P4-Ubuntu <<>> @127.0.0.1 mycoolzone ns
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 15928
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;mycoolzone. IN NS
;; ANSWER SECTION:
mycoolzone. 60 IN NS dns-1.mycoolzone.
mycoolzone. 60 IN NS dns-2.mycoolzone.
;; ADDITIONAL SECTION:
dns-1.mycoolzone. 60 IN A 10.152.0.3
dns-2.mycoolzone. 60 IN A 192.168.0.10
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Tue Oct 30 11:43:02 AEDT 2018
;; MSG SIZE rcvd: 111
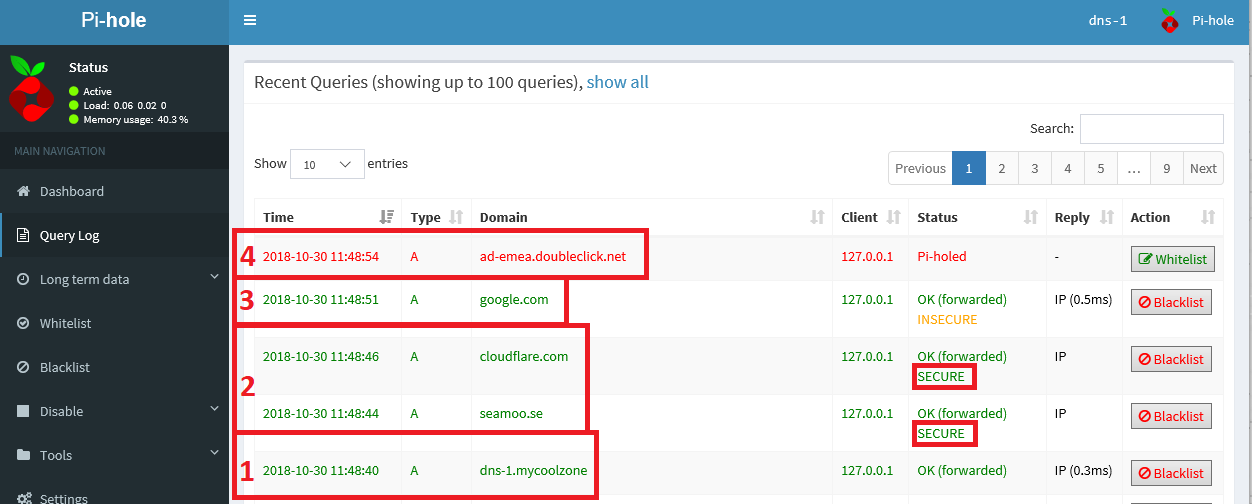
- To test everything out, just start querying your DNS for various domain names and check out the Query Log in Pi-hole.
You should see:
- Local zones forwarding to BIND
- Remote DNSSEC enabled zones forwarding to cloudflared and coming back as SECURE
- Remote non-DNSSEC enabled zones forwarding to cloudflared (coming back as INSECURE)
- Pi-holed enabled domains being black-holed.
I hope you’ve enjoyed this quick tutorial. If you find any errors in the steps I have provided or have any feedback, please feel free to email me. I will probably write some future articles on how to improve this entire process, and realistically its probably not that hard to script up. If only I knew how to write scripts properly :-P
Enjoy!
Thanks to Patrick for pointing out an incorrect configuration, which has been updated!